These are all machines I have worked on in the past—hover for more details.




Thanks to Mark Richards for the photos.
These are all machines I have worked on in the past—hover for more details.




Thanks to Mark Richards for the photos.
If you are a Virgin Media customer then by now you will probably have had a long email from them explaining that their mail system is changing and you don’t need to worry as it will all be transparent and continue working like before. That is not entirely true because if you look into it carefully you will find a number of things have changed and not all for the better.
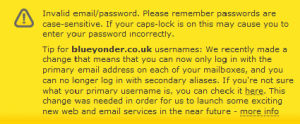 But there is a catch—If you have set up aliases to your unmemorable email address like your name instead of jsbr123456 which is the style of the old TeleWest accounts then you can’t be sure which one it wants. In my case it would only accept the alias. This applies to any secondary accounts you may have set up as well (each with their own password).
But there is a catch—If you have set up aliases to your unmemorable email address like your name instead of jsbr123456 which is the style of the old TeleWest accounts then you can’t be sure which one it wants. In my case it would only accept the alias. This applies to any secondary accounts you may have set up as well (each with their own password).The other place you may want to login is the eBilling system (because it saves you £1.25 a month). This is also done from the “My Virgin Media” main page but has a separate login button near the top right. This also requires an email address and a password (called a PIN) but, surprisingly, the email address does not have to be a Virgin one, it can be anything.

The Telegraph has a slide-show series of Airport Security cartoons.
Today is Safer Internet Day 2010 and [one of] the slogan[s] being promoted is “Zip it, Block it, Flag it”; I suppose the principle is ok but this is not the language that kids understand however we are stuck with it. What it means, and I had to look it up, is Zip it—Keep stuff private, Block it—Block nasty people, Flag it—Tell someone if anything bothers you. There is more detail, but that is the gist of it; make it too complex and they won’t remember at all. Seeing as this program was announced back in December by the Prime Minister, it is not exactly prominent!
Anyway, I would like to add another one, not for the kids, except perhaps the older ones, but for the parents—Log it.
Most instant messaging (IM) and chat systems have a mechanism that allows a permanent (private) log to be made of all conversations. Switch it on. That way, if there is any doubt or worry then it can be reviewed and, when it is all in one place, trends and tendencies can be spotted more easily. Of course, for young children it is only a reminder because you are always there with them when they are on line **AREN’T YOU**. Older ones are entitled to a bit of privacy so if there are any concerns then you can discuss it with them and review the log together. Without the log there is no evidence that you can see (there are server chat logs which the police can use if an offence is suspected). But, beware, some chat systems also have public logs available where conversations can be seen by anybody. This is not usually a good idea.
Footnote: these are really rotten web sites, they don’t work properly with all web browsers, some make sounds which you can’t turn off and one feature only works with IE 8, a browser only used by 15% of users. The real web site is ceop.gov.uk but there are bogus ones at ceop.org.uk and ceop.co.uk designed to mislead you.
…with a nod to Marc Bolan for the name.
When looking at problems I was having with the tagging of MP3 files recently, I had the need for something that would unambiguously tell me exactly what tags were in a file and to verify that they were changed when I thought they should be. Although there are a lot of music library programs out there I needed something that would tell it as it was and never attempt to change anything.
So I wrote this program; and very big it turned out to be. Meta data in music files is much more complex than I expected.
Like all my stuff it is a command line program, so no fancy graphical interface and, at the moment, it is compiled for Intel Macs and (since v1.4) Windows. I know that it does work on Sun Sparc Solaris. It is probably good for other platforms too and the source code is supplied for you to port if you want to try. The output is quite voluminous, particularly if verbose mode is specified so be prepared to wade through a lot of information.
Since I first wrote it, it has extended in scope and now reports…
I would like to go to other formats if I can get the information, particularly Apple & OGG sound files and GIF & PNG graphics files. I will be adding basic disk file meta data such as permissions and creation & modification dates pretty soon, though I have a feeling that this will be less portable.
I have created a static support page for the program which includes download links and full instructions on how to run it. In a later posting I will be reporting on some of the things I discovered by using it.
Updated: 23 Feb 2010 to v1.2
Updated: 8 Jan 2012 to v1.4
When I was a child, one of the things I loved to receive at Christmas and birthdays were gift cards. In those days it was book tokens and it meant that I could get something that I wanted rather than chosen by a rarely seen aunt who had forgotten how old I was. Later on it became record tokens but after a while these became a problem because few shops would take them where we lived. However, I think book tokens are still going strong.
In latter years everyone got into it and there was a big growth in store tokens. Everyone from the big department stores to smaller specialist chains had their own gift tokens; even some individual shops did it.
Recently there has been a move away from the denominated slip of paper with banknote like swirls, embossing, holograms and markers to a plastic card that looks like a store discount/loyalty/charge card. With this have come some security problems which are causing many people grief. The victims can be the shop or the customer and the perpetrators can be the staff, the public or third parties. I will concentrate on the problems for the customer because they have no control over the system.
The cards themselves are low security. They have a number which is duplicated by a bar code and sometimes by a magnetic stripe. Some cards also have a PIN which is initially concealed by a scratch-off covering. When the card is purchased it is “loaded” with money but this does not get recorded on the card itself but onto a central computer system. When goods are purchased with the card then the cost is deducted and any balance remains in credit. In order to provide the customer with documentary evidence a receipt is issued every time a card transaction takes place which shows how much is left on the card and this can also be checked at any time, either in a branch of the shop, by telephone or online.
How can you be conned? There are a number of holes in the system from old fashioned deception though to weaknesses in the system.
The cure for all of these is to observe closely everything that happens. When you get the card initially make sure the number on the card matches the one on the receipt and write that number on the inside of the gift wallet. Then when each transaction takes place, make sure the new receipt matches the same number and the card number is still the same. Also demand to have the empty card back, it is yours. If there is a significant amount of money on it then separately check the value using the phone/online system or another cashier.
There is one final scam which is enabled by the poor system design and there is not much that the customer can do about it.
The flaw in the system here is that there is no interaction with the real card like there is with a Chip-and-Pin credit card. For online transactions they use the scratch-off PIN to verify that you actually have the card but in the shop there is no similar verification if you are on the inside—i.e. staff.
These observations were made on one brand (the M&S store card) but I am not picking on that one in particular because they all have similar problems. Perhaps there are some with real security but I haven’t seen one. These are being treated like real money, they are already as vulnerable as cash because there is no recovery if they are lost, yet the value can be spirited away from you without you even knowing.
Three years ago, back at the start of 2007, I wrote about the Digital Dividend and the impact on the use of radio microphones. The conclusion then was that there was no planned effect on the unregulated channel 70 and that they were proposing that the currently licensed channel 69 would also become deregulated. Well they had their review and after public consultation changed their minds a little and proposed to leave channel 69 as it was, a licensed band (see para. 1.43). OK.
But it seems that they have now discussed it in Europe and collectively they have decided to clear the 800MHz completely—including channel 69. The detail of the proposal is that users of channel 69 are to be moved to channel 38. This will have an enormous impact on the entertainment industry and other users of radio microphones, talkback and instrumentation systems (collectively known as PMSE). That includes a proportion of churches that use licensed bands. Most of them will be using the unregulated channel 70 and that is not going to change but where there are interference problems or more than four frequencies are required then they will be using channel 69 and this will make a difference. It is estimated that one in eight will be affected. Effectively, most of the old gear will have to be thrown away and new stuff purchased because the frequency change from 854 to 606MHz is too great to allow simple re-tuning in most equipment. Mine can only be internally changed (at some cost) down to 690MHz channel 48. The situation is so serious that the Church of England has joined the campaign group Save our Sound to lobby government to change their minds or compensate users.
On top of that, channel 38 was previously used by radio astronomers and it is not certain that they are clear of it yet. Certainly its use for radio microphones is regionally limited and is not available in the North-West of England until 2012. There are other channel moves proposed but they will affect the larger commercial organisations rather than smaller operations such as churches.
This one must justify the name, though I don’t know how that package got involved as it is not one I use (and I can’t see BlueYonder/VirginMedia using it either). It was sent from my BY account, possibly via webmail, to Mary’s address—and turned up back with me over six months later. Nuts must be short at the moment.
A friend pointed out the recent article in the Guardian about the dark side of the internet. Whilst it is quite a good article it both only just skims the surface and rather heavily emphasizes the negative aspects as if it was all deliberate and malicious. Here I will provide some definitions and separate out the completely different aspects of the internet that cannot be seen. Much of this is in the original article but it is overshadowed by a little journalistic hyperbole. I have also added some reference links, something newspapers always leave out.
This phrase is used to describe the hard to access parts of the internet using any protocol. This could be caused by router configuration or firewalls. MILNET is a notable deliberate example, kept separate for obvious reasons. The majority of corporate and domestic computer networks also fall into this category either by the use of deliberate managed firewalls or simple NAT based routers with limited port forwarding configured. Another proportion consists of machines that people have forgotten about and are still running but the connections are damaged in some way.
There are Web sites that are hard to find by conventional search. This could be because of dynamic content,
lack of incoming links, registration/login requirements, deliberate banning of search bots, scripted links and non-indexable media formats such as audio, video and images. This limits their presence in standard search engines so cannot be found by conventional means. It is considered to be many orders of magnitude larger than the surface web indexed by search engines. To a limited extent this has been addressed by human based searches such as StumbleUpon, manual submission to search engines like Open Directory and semi-automatic systems using things like Google Sitemap. That is assuming, of course, that the owners want them to be found. The majority of this information is proprietary information accessible only by companies and their customers and academic data used by researchers. Also there are old web sites, abandoned and unloved that simply don’t work any more and can’t be indexed. Think Geocities or Tripod. It may also contain a small amount of content that some may regard as illegal. The reason it is likely to be small is that it requires a more stable, permanent and sophisticated infrastructure than underground organisations can sustain and, in any case, the external port is publicly visible.
This is where the author started. They are network connections using protocols other than HTTP, usually for private P2P file sharing but can also support forum and chat type connections. The best known are Waste (by Nullsoft) [now withdrawn] and Freenet and form a very small proportion of the internet. These networks are often hosted on what would normally be regarded as personal desktop machines rather than centralised servers and form a rapidly and dynamically changing mesh as machines come and go. In this respect it is similar to other P2P systems but no files exist in one place in their entirety, they are fragmented and scattered. The services are founded on principles of free speech which may be beyond what some people would regard as legal or moral. There is no central organisation and therefore no censorship of any kind. A proportion of the material on the darknet would be regarded as illegal by some governments. This ranges from dissident material placed and accessed by citizens of repressive regimes, through music and video file sharing in contravention of copyright up to illegal pornographic material and terrorist aids. It should remembered that free speech facilities are used to do good as well as evil (put those two in whichever order pleases you) and it should be noted that Google is one of the largesst sponsors of Freenet.
The latter systems should not be confused with archaic protocol networks from the early days of computing which are still running. These include Fidonet, Compuserve, IRC and Usenet (sometimes called Newsgroups). They require specialised software to access them but are only dark because they have dropped out of mainstream usage. One could say that modern but proprietary protocols such as AIM, MSN & Skype fit this category but they are well known and don’t generally hold permanent content.
This is one for the boys—not. We have discovered that it is mostly the girls who are caught up by the Farmville type scams but this time it is the boys using Facebook that have to look out. There is a very sophisticated worm about (a worm is like a virus but crawls through web sites rather than directly between PCs). If you see someone’s profile picture has become a rather curvaceous girl in a Bikini then *don’t* click on it. If you do, then three things will happen. First you will be taken to a web site which contains rather a lot of porn. Secondly, that web site will download a lot of nasty stuff to your computer such as programs that steal account details. Thirdly, your profile will be changed to include this picture so as to attract other mugs victims. I said sophisticated at the start because it uses a lot of different techniques to trap you, from the initial social engineering making you think with the wrong part of your body through to clickjacking which is a page layout technique where you think you are clicking on something innocent (ha!) but actually saying yes to something important hidden underneath. As Roger Thompson says in a parody of Trooper Truth, “Keep safe, folks.”