A common fault with these keys is that one of the buttons stops working. You can tell when this is a fault with the key rather than the car because the led stops flashing. If both buttons have failed then first try the obvious and test the battery and make sure the contacts are clean. If so then you need to resort to one of two drastic solutions; buy another one (about £130) or repair it.

This is the type of key we are talking about, it is the type with two buttons and the safety slot in the end, not the proximity type. There may be other models that use a similar key, I have seen one with three buttons for instance, but I don’t know if they have the same weakness. The fault with these keys is that they use surface mount micro-switches and the “lock” one seems to be on a vulnerable part of the board which perhaps flexes and it drops off. Often you can hear it rattling loose inside.
The tools you will need are a good strong Stanley knife, a soldering iron with a very small tip (1mm or less), some long or curved-nose pliers, a strong magnifier and some super-glue.
The first task is to get inside. These are not clip-together cases, they are glued all round and on some internal ribs as well. On the photograph of my one below (click for a larger image without my annotations), I have marked the glue lines in red. The blue dots are unglued guide posts. With a strong Stanley knife and starting at the point marked “A” you can carefully cut along the edge, try to cut if you can as it doesn’t split very well—and watch your hands as the blade is liable to slip. When you reach the first bend “B” go back and do the first internal rib, then you can move round peering in the crack to see what to cut next. Be careful not to damage the components or the circuit board. A close inspection of the pictures shows the things to avoid, it is really a matter of patience, care and brute force.

As you can see, mine opened upside down, so the next step is to cut under the battery clip to separate the circuit from the case; I used a small kitchen knife to get in there.

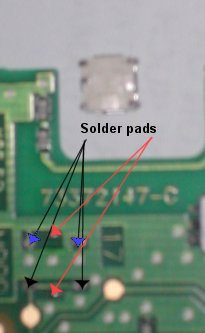
So you should now have all the parts laid out including a loose button switch. This switch has a contact on each corner, two fold-under lugs to hold it together and two other lugs to help it stick to the board (ha! ha!). Sorry, the resolution of our camera is not good enough to see this detail. Near the centre of the circuit board you have a corresponding space with two pads on the earth plane at the top (arrowed blue), two on a track leading to the IC at the bottom (arrowed black) and two isolated holding pads (arrowed red). The orientation of the switch is important, the wrap around lugs MUST be to the sides.
With your fine tip soldering iron, clear up and tin all the contacts on the switch. Similarly clean the circuit board pads. You are well away from any delicate components here so there is not a lot of risk. Make a small solder bead on each pad. When I say small I mean small; I used a jewellers eyepiece to see what I was doing, scary with a hot soldering iron inches from my face.
Now lay the switch on top and test that it works by holding the battery in, and pressing the button. If you get the switch the wrong way around, the light will be on without pressing the button. Satisfied that it works you can solder the switch into place—holding the switch down with long pliers, touch the soldering iron to each corner and the top/bottom edges to get the solder to bridge the gap in six places. You may need to go round more than once as the component beds down to the surface. Test it again. As a final touch, I dribbled a bit of super-glue under the switch as an attempt to hold it more securely.

Now clean up the plastic parts with a knife, removing all loose bits and get the halves to mate together tightly without the circuit. You will also need to clean up the plastic part of the battery clip. Lay the circuit into the back cover, there should be two positioning pegs to hold it in place. Apply a drop of glue to the battery clip to secure it and leave it for a few moments to set. Finally run a bead of glue around the outside edges and the main internal rib, bring the parts together and clamp (clothes pegs) or weight it until it sets. How many of the original lines you do depends on if you are likely to want to undo it again but I would suggest omitting the front of the battery clip.
For the technical, the numbers on the components are: the big round piece (transmitter coil?) is 50751, the DIL package (encoder?) is Phillips PCF7947AT with other numbers 16793102 and DnD00350. The small silvery unit (oscillator crystal?) has EPC05, R727 and M5MN. A Google search didn’t turn up much.












 Webmaster
Webmaster